
Metasploit module to steal iPhone backups YouTube
Metasploit is a hacking "framework" that was developed by HD Moore in 2003. Metasploit is simply a repository of exploits that have been packaged to work with a common formatted syntax to exploit. Custom exploits can be written and added to metasploit to be used. Metasploit exploitation is a very simple concept.

Install metasploit on you iPhone YouTube
While Metasploit standardizes with the JtR format, the hashcat library includes the jtr_format_to_hashcat_format function to translate from jtr to hashcat. Cracker Modes. Each crack mode is a set of rules which apply to that specific mode. The idea being any optimizations can be applied to that mode, and reset on other modes.

MetaSploit on iPhone (iOS 13 Jailbreak) iPhone Tutorials
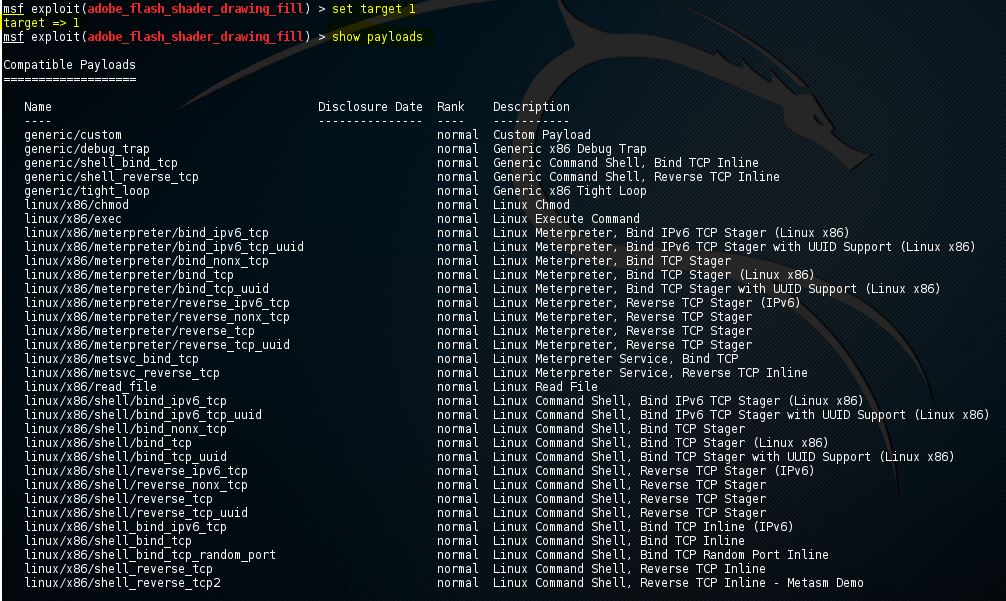
Metasploit is a popular open-source framework for creating, testing, and deploying exploits. It is used by hackers (ethical and otherwise) and security researchers to test the security of machines, networks, and infrastructure. Metasploit's collection of exploits, payloads, and tools to conduct penetration testing can speed up the testing.

Hacking with Metasploit 메타스플로잇으로 해킹하기! YouTube
Metasploit is an open-source framework written in Ruby. It is written to be an extensible framework, so that if you want to build custom features using Ruby, you can easily do that via plugins. Rapid7, the company behind Metasploit, offers a premium version of Metasploit with advanced features.

Metasploit Basics for Hackers, Part 1 Getting Started with Metasploit5
apt [APT 0.7 Strict] (via Cydia) SSH client (I use iSSH; via App Store) First, make sure everything is updated and that you have subversion installed: apt-get update. apt-get dist-upgrade. apt-get install wget subversion. Once that's done, we'll need to grab Ruby and iOS dependencies for Metasploit Framework to run.

Metasploit Basics for Hackers, Part 1 Getting Started with Metasploit5
Hack Like a Pro: How to Exploit and Gain Remote Access to PCs Running Windows XP ; Forum Thread: Install Metasploit Framework in Termux No Root Needed M-Wiz Tool 0 Replies 3 yrs ago How to Hack Like a Pro: Getting Started with Metasploit ; Metasploit: EXPLOIT FAIL to BIND 0 Replies
Comandos Metasploit Tutoriais de Hacking Never thought about that
Metasploit is a penetration testing framework that makes hacking simple. It's an essential tool for many attackers and defenders. Point Metasploit at your target, pick an exploit, what payload.
Hack Like a Pro The Ultimate Command Cheat Sheet for Metasploit's
Google Project Zero security researcher Ian Beer has revealed that, until May, a variety of Apple iPhones and other iOS devices were vulnerable to an incredible exploit that could let attackers.

How to hack metasploit using DLL By YouTube
iPwn is a framework meant for exploiting and and gaining access to iOS devices. It also has an extension that is a mini-framework called 'iSteal' that is meant for post-exploitation (after you get access to the device). This description will walk you through the different ways and steps to get access to an iOS device and harvest information.
Metasploit commands Hacking Tutorials
Crack Interface lockscreen, Metasploit and More Android/IOS Hacking. geolocation lockscreen bypass webcam-capture android-hacking ios-hacking ip-logger bruteandroid bypass-lockscreen Updated Nov 10, 2023; HTML. This is An Offensive Hacking Tool which can be used by hackers and for penetration testing purposes. Hack Responsibly!!!!!

How To Use Metasploit Framework For Hacking YouTube
After a bit of fiddling around with various ruby package versions, its seems like the following combination works well with the latest version of Metasploit 4.4.0-dev (as of May 2012). Of course, you need a jailbroken iPhone or iPad, with apt, OpenSSH server and a SSH client, such as iSSH.
Como instalar Metasploit para Hacking YouTube
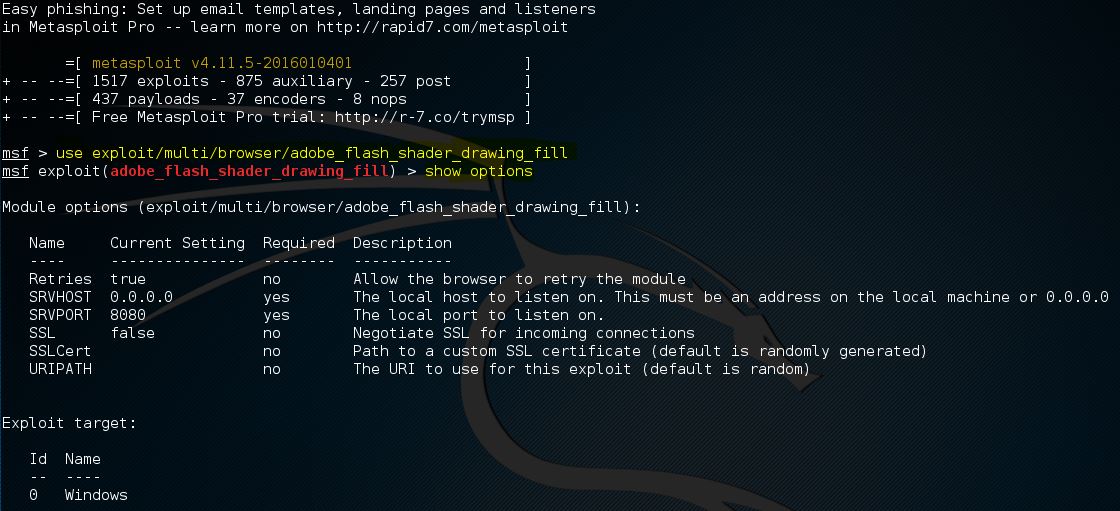
Metasploit 3.0 now has Apple iPhone shellcode, with "payloads" for writing exploits using the Metasploit framework. "The addition of iPhone payloads to Metasploit makes it easy for a researcher to.
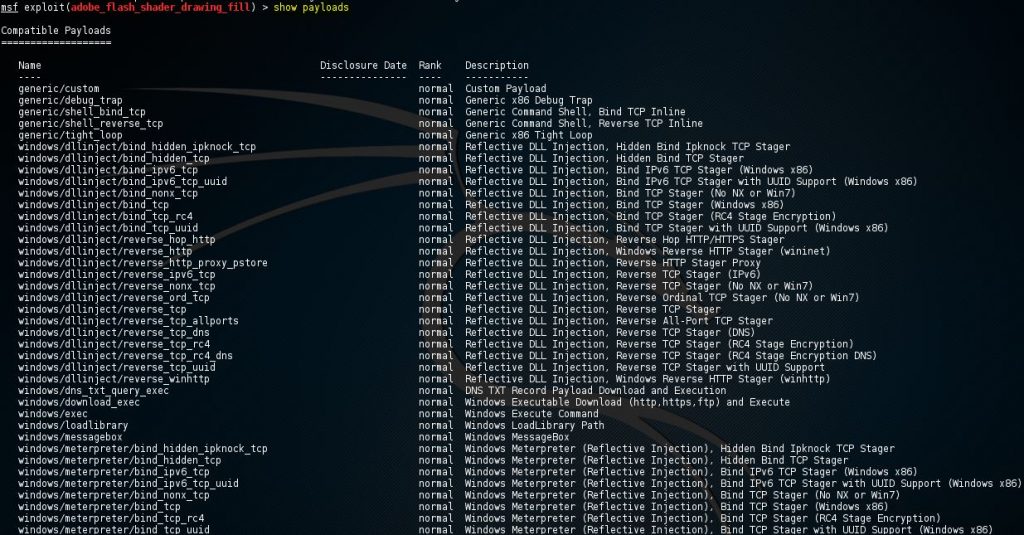
Metasploit commands Hacking Tutorials
HD Moore, one of the developers of the Metasploit pen-testing (and hacking) tool, has posted exploits and detailed instructions on how to attack an iPhone. The information takes hackers — and.

iPhone with metasploit and SET(Social Engineering Toolkit) YouTube
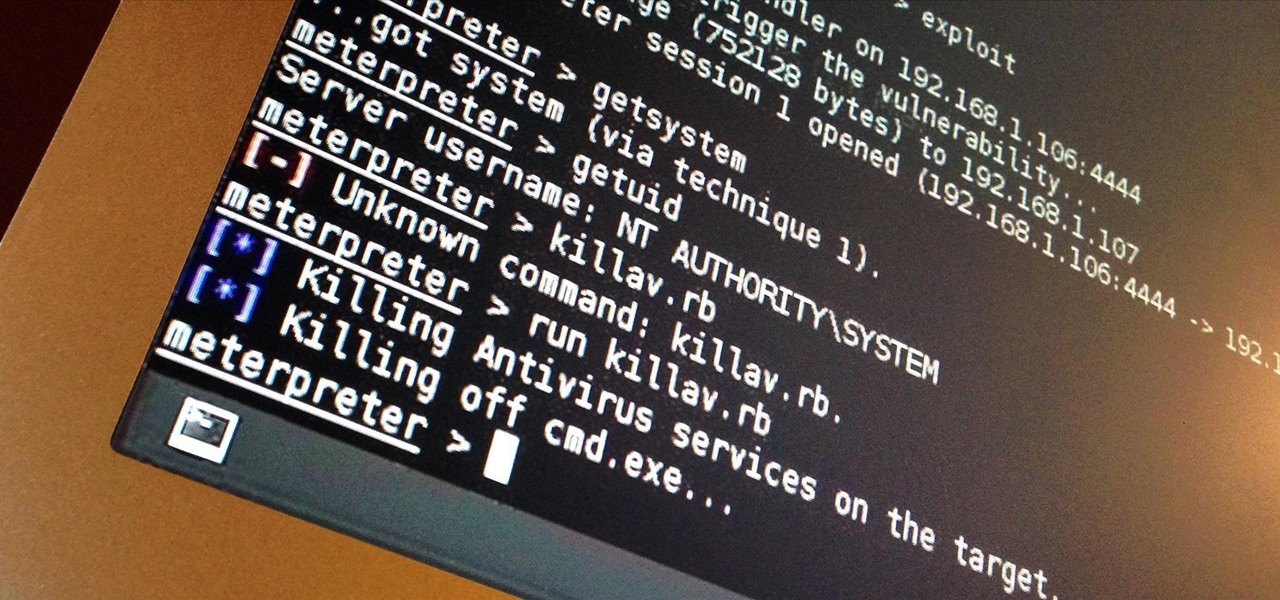
How To Hack a Phone, Android or iPhone Using MetasploitMetasploit is a powerful open-source penetration testing framework that allows security professionals and ethical hackers to identify and exploit vulnerabilities in computer systems, networks, and applications. It is primarily used for testing the security of systems and assessing potential risks.Here's an overview of how Metasploit works.
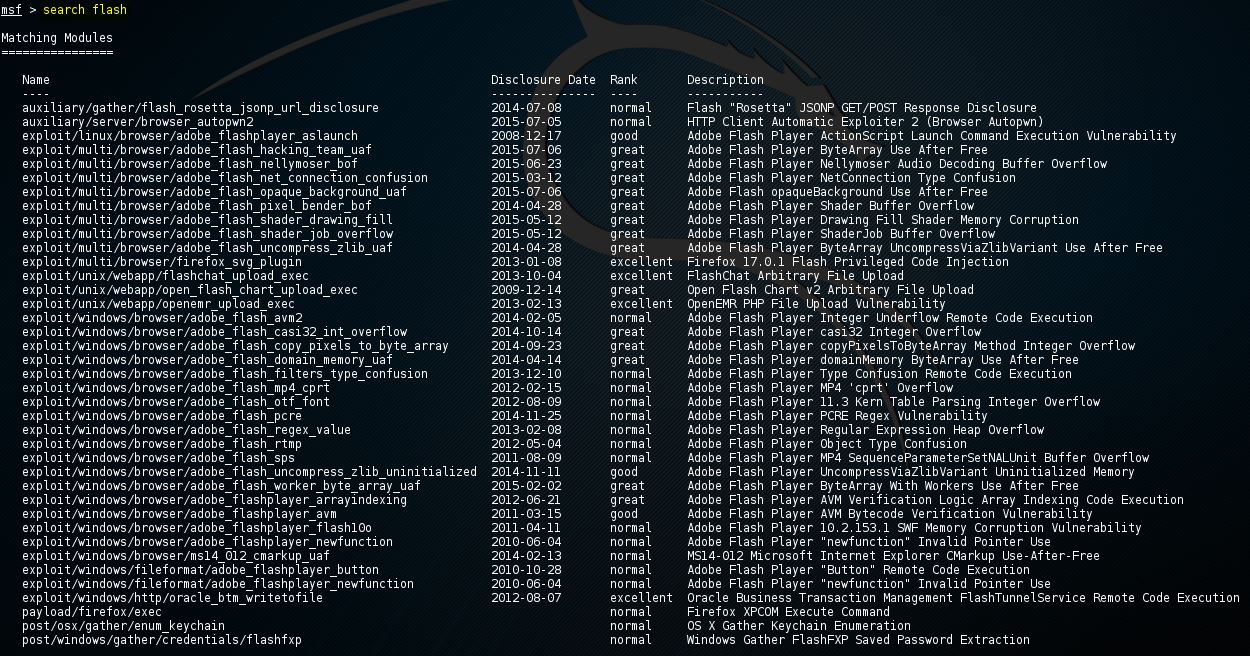
Comandos Metasploit Tutoriais de Hacking Never thought about that
In this video we're learning how to install the MetaSploit Framework on iPhone (or iPad) for ethical hacking. Let's check it out!You will need a jailbroken d.

hack IPhone with Backtrack5 and Metasploit armitage [EyesOpen] YouTube
Where To Learn Ethical Hacking & Penetration Testing; Exploits, Vulnerabilities and Payloads: Practical Introduction; Solving Problems with Office 365 Email from GoDaddy;. This page has been produced using Metasploit Framework version 6.1.24-dev. For more modules, visit the Metasploit Module Library. Go back to menu. SEARCH THIS SITE. Search.